Blockchain terms & concepts
Blockchain nodes, Consensus Mechanisms, Bridges, Metrics, Merged Mining, Forks, Types, Addresses, Wallets, Record-keeping Models. Use-cases.
1. What is a Blockchain?
A conceptual overview of a Blockchain Network
A blockchain:
is a linear, chronological structure
consists of blocks of data (transactions) that are chained together.
Blockchain is best suited for 1 use case - smart asset lifecycle management.
Blockchain increases transparency and reduces the need for intermediaries in financial use cases.
Distributed Ledger Technology (DLT)
While Blockchains have a linear chronological structure, DLTs can have different structures, such as:
Graph e.g. IOTA
Mesh e.g. Holochain
Tree e.g. Corda
DLTs are suited for multiple use cases such as:
Supply Chain Management
Identity and Verification
Healthcare
Government and Public services
All Blockchains are DLTs, but all DLTs are not Blockchains
Blockchain Nodes
A blockchain is a transaction database shared by all nodes participating in a network.
A node is a computer that runs the blockchain's software to validate & store the complete history of transactions.
A full copy of a blockchain contains every transaction ever executed in the native coin (e.g. ETH) and tokens (e.g. BAT) created on the blockchain.
Transactions are bundled in blocks.
Each block contains a record of some / all recent transactions. Each block also contains a reference to the block that came immediately before it.
Mining
In a Proof of Work blockchain like Bitcoin, each block also contains an answer to a difficult-to-solve mathematical puzzle.
Mining is the process of competing to be the next to find the answer that "solves" the current block.
New blocks cannot be submitted to the network without the correct answer.
The mathematical problem in each block is very difficult to solve, but once a valid solution is found, it is very easy to verify.
Every block contains a hash of the previous block.
This creates a chain of blocks from the first (genesis) block to the current block.
It is extremely difficult to modify a block once it has been in the blockchain for some time because every block after it would also have to be generated again.
The Layers of a Blockchain Network
Layer 0: Infrastructure or Physical Layer
This consists of the hardware, software, and networks that enable the functioning of the blockchain.
Layer 1: Logical Layer
This consists of the protocols, rules, and standards that define the functioning of the blockchain.
Layer 2: Application Layer
This consists of the protocols, applications, and services that build on top of the basic building blocks provided by layer 1.
Layer 3: User Interface Layer
This consists of the interfaces, applications, and services that enable users to interact with the blockchain and access its underlying functionality.
The infographic below depicts the 4 layers of a Blockchain Network.
2. Types of Blockchains
Layer-0 Blockchains
Layer-0 blockchains enable developers to create custom blockchains.
Example: Polkadot enables the creation of sovereign blockchains with their own tokens.
These parachains plug into a single base platform called the Relay Chain which is responsible for shared security, consensus & cross-chain interoperability.
Other examples of L0 are Cosmos and Horizen.
L0 blockchains are different from Blockchain Frameworks like Multichain and Hyperledger Fabric.
Frameworks are open-source software that enable developers to create custom blockchains.
Remember: Layer-0 blockchains are networks while Frameworks are software programs.
Layer-1 Blockchains
Layer-1 blockchains validate & execute transactions without the need for any external network.
Examples: Bitcoin, and Ethereum Mainnet.
Layer-2 Blockchains
Layer-2 blockchains are "sidechains" built on top of Layer-1 blockchains.
The underlying Layer-1 (e.g. Ethereum Mainnet) provides decentralization & security, while the Layer-2 (e.g. Polygon PoS) provides scalability.
Permission-less blockchains
Anyone can participate on public / permission-less blockchains without restrictions.
Examples: Bitcoin, Litecoin, Ethereum.
Permissioned blockchains
Various controls can be set in a private / permissioned blockchain.
Example: Hybrid Finance Blockchain where permissions such as connect, send, receive, issue, create, mine, activate, and admin can be set.
Federated blockchains
In a federated / consortium blockchain network, the validation process is controlled by a select set of nodes.
EVM-compatible chains
Ethereum Virtual Machine (EVM) is "the environment in which all 'Ethereum' accounts and smart contracts live".
Smart contracts are programs that run automatically when some pre-defined conditions are met.
EVM compatibility is the ability to write & deploy smart contract code that are:
compatible with EVM, and
can be recognized by Ethereum nodes.
Examples of EVM-compatible blockchains are Avalanche, Binance Smart Chain, Fantom, and Polygon.
3. What are Blockchain Nodes?
A conceptual overview of a Blockchain Node
A blockchain node is a computer that runs the blockchain's software to validate & store the complete history of transactions on the network.
Blockchain nodes constantly exchange information on new transactions & blocks.
Archival Full Nodes
They are the most important. They host the entire blockchain, validate blocks & maintain consensus.
Pruned Full Node
A pruned full node first downloads the entire blockchain and then deletes blocks beginning with the oldest block till it holds only the most recent transactions up to the size limit set by the operator.
Masternodes
Users run masternodes to earn network rewards. Some amount of native tokens has to be "locked" by masternode operators.
Light nodes
A light node does not hold the full copy of the blockchain. It saves download time & storage space by only downloading block headers.
Cold nodes
They are used for signing transactions offline and storing private keys away from the network.
Lightning nodes
They reduce the load on the network by enabling off-chain transactions. These nodes enable faster and cheaper transactions.
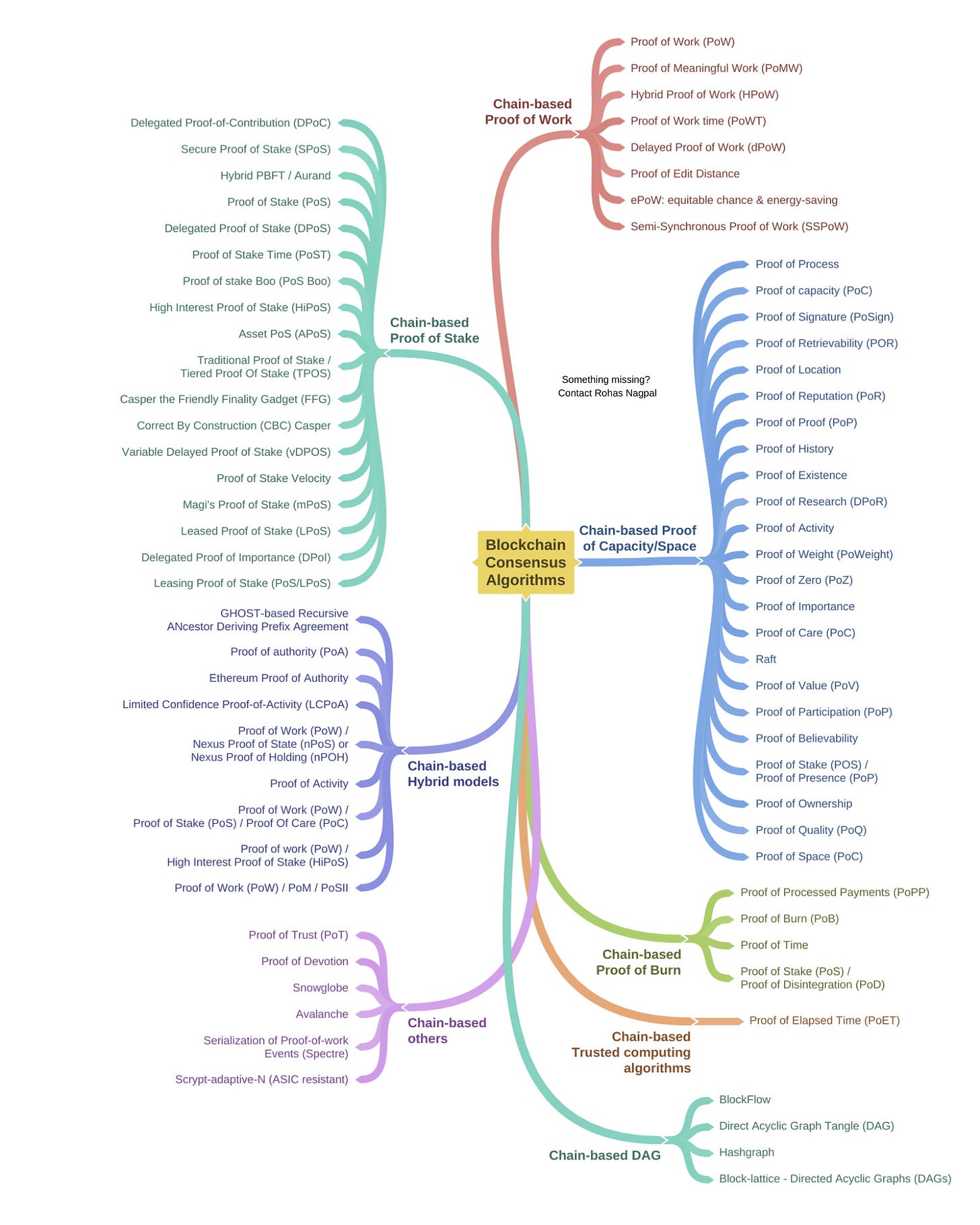
4. Blockchain Consensus Mechanisms
Consensus algorithms are the heart of blockchains.
They enable network participants to agree on the contents of a blockchain in a distributed and trustless manner.
Today there are over 75 consensus algorithms.
Proof-of-Work (PoW)
This was the world’s first consensus algorithm. Miners "solve" mathematical puzzles by investing in electricity and computational power e.g. Bitcoin.
Proof of Stake (PoS)
Holders "lock" a number of coins as a "stake" and are randomly assigned validation rights for a new block e.g. Algorand.
Hybrid PoW / PoS
This brings together the security of Proof of work and the governance & energy efficiency of Proof-of-Stake e.g. Decred.
Proof-of-Work-Time (PoWT)
This features a variable blocktime that scales with mining power. The blockchain speeds up with power increases. This mechanism scales the blockchain well and increases transaction speed with power.
Proof of Meaningful Work (PoMW)
The energy invested by miners' is used for calculations that benefit public scientific research projects (e.g. medical research for cures, chemical research, and astrophysical simulations).
Proof of Elapsed Time (PoET)
Each node goes to sleep for a random "wait time" generated by the network. The node with the shortest wait time wakes up first and commits a new block e.g. Hyperledger Sawtooth.
Proof-of-replication (PoRep)
Storage miners prove 2 things:
that they are using space to store replicas of data, and
that the data can easily be accessed.
They get rewards in exchange for their storage space e.g. Filecoin.
Delegated Proof of Stake (DPoS)
Holders "lock" a number of coins as a "stake" but outsource validation to "delegates" selected based on reputation and trustworthiness e.g. Bitshares.
Proof-of-Spacetime (PoSt)
Randomly selected miners prove that they have been physically storing data for a certain period of time e.g. Filecoin.
Proof-of-burn (PoB)
Miners reach a consensus by sending coins to an "eater" or "burn" address. This permanently eliminates coins from circulation, reduces inflation, and validates transactions e.g. Slimcoin.
Proof-of-Authority (PoA)
Identified, known, and credible validators produce blocks in this system. It is meant for private & enterprise blockchains.
This mindmap shows 82 blockchain consensus mechanisms divided into 9 categories.
Information source: Blockchain Consensus Encyclopedia Infographic
5. Blockchain Bridges
Let's say you live in India and are traveling to Singapore. In India, we use Indian Rupees (INR) while in Singapore they use Singapore Dollars (SGD).
So you could convert some money from INR to SGD using a bank. Or you could use an international card that enables you to pay in SGD when you are in Singapore.
This is simple in the world of banks. But a lot more difficult in the world of Blockchains.
Ethereum Mainnet and Terra are two independent Blockchains. They have different rules and consensus mechanisms. The native token of Ethereum Mainnet is ETH while that of Terra is LUNA.
Now suppose that you have a bunch of LUNA on Terra, but want to use it on the Ethereum Mainnet. How do you do that?
That's where a Blockchain Bridge comes into the picture. You could use the Terra Bridge to buy Wrapped Luna (WLUNA) which is an ERC-20 token native to the Ethereum Mainnet.
In simple terms, here's how a typical bridge works:
It receives one type of crypto e.g. LUNA.
It locks this LUNA as a deposit.
It "mints" an equal amount of another crypto e.g. Wrapped LUNA and releases it on another blockchain e.g. Ethereum Mainnet.
Hacking Blockchain Bridges
Because bridges hold a ton of crypto, they are juicy targets for hackers.
And because writing the code for bridges is insanely complex, hackers are having a field day plundering them.
When a bridge gets attacked, the hacker withdraws crypto from one side of the bridge, e.g. Wrapped LUNA, without depositing anything on the other side e.g. LUNA.
One of the biggest crypto attacks took place in March 2022 when the Ronin bridge, built for Axie Infinity, was hacked for $600+ million in ETH and USDC.
Ronin worked "off-chain" - it interfaced with the blockchain but existed on external servers that were not a part of the blockchain.
Ronin relied on 9 validator nodes, of which 5 nodes were needed to validate transactions.
The hackers exploited code vulnerabilities and also used social engineering.
Another major Bridge hack targeted Wormhole which supports 6 blockchains - Terra, Solana, Ethereum, Binance Smart Chain, Avalanche, and Polygon.
The cost of the hack was $325 million.
Bridges can be Trusted or Trustless
A Trusted Bridge depends upon a central entity and you lose control of your cryptos when you use it.
A Trustless Bridge operates using smart contracts and you remain in control of your cryptos.
6. Blockchain Metrics
Throughput
Throughput is the number of transactions per second that a Blockchain consensus algorithm can process.
Fault tolerance threshold
Fault tolerance threshold is the upper limit of faulty nodes that directly impacts the performance of a blockchain consensus algorithm.
Finality
Finality (also called Latency) represents the time it takes for a transaction to be settled in the "ledger" of a blockchain.
Scalability
Scalability is the ability of a blockchain to expand without degrading performance.
Bitcoin
Throughput: 7 tps
Finality: 60 min
Threshold: 51%
Ethereum Mainnet
Throughput: 14 tps
Finality: 6 min
Threshold: 51%
Polkadot
Throughput: 1500 tps
Finality: 60 secs
Threshold: 33%
7. What is Merged Mining?
Merged mining is the process of mining two or more blockchains at the same time.
Essentially the same proof of work can be used on multiple chains.
Merged mining is technically called Auxiliary Proof-of-Work (AuxPoW).
The concept is that the work done on one blockchain can be leveraged as valid work on another blockchain.
The blockchain that provides the proof of work is called the parent blockchain.
The blockchain that accepts the proof of work as valid is the auxiliary blockchain.
To perform merged mining, all the involved blockchains should be using the same algorithm.
Since Bitcoin uses SHA-256, any other blockchain that uses SHA-256 can be mined along with Bitcoin subject to some technical implementations.
Merged Mining increases the profitability and performance of mining and is hugely beneficial for miners.
Some examples of merge mining:
Dogecoin and Litecoin
Bitcoin and RSK
8. What are Blockchain Forks?
A "fork" is when a single blockchain splits into two.
Forks can be categorized as hard forks or soft forks.
Hard Fork
A hard fork is the result of an extensive network change. Each node has to upgrade its software to be compatible with the new processes.
If a node does not upgrade its software, it will be on a different blockchain.
Soft Fork
In a soft fork, nodes running the old software are still able to validate transactions. Software forks are backward-compatible.
Ethereum Fork
In 2016, the world's first decentralized autonomous organization (DAO)raised about US$ 150 million worth of ETH through a token sale.
But a hacker exploited a bug in the "smart contract" and siphoned out all the money!
A hard fork rolled back Ethereum's history to before the hack.
This reallocated the hacked ether to a different "smart contract" and allowed investors to withdraw their funds.
The purists hated this, which led to Ethereum splitting into 2 blockchains: Ethereum and Ethereum Classic.
Bitcoin Cash Fork
In July 2017, Bitcoin (BTC) miners representing more than 80% of the Bitcoin computing power voted to incorporate the SegWit2x (segregated witness) technology to improve Bitcoin.
Many miners and developers, who did not want SegWit2x to be introduced, initiated a hard fork and created a new blockchain and cryptocurrency - Bitcoin Cash (BCH).
9. Blockchain Addresses
When you buy gold or real estate, you actually get physical possession.
Blockchain assets (e.g. cryptocurrencies) are very different.
On a blockchain, we all need a key pair - public key & private key.
This key pair is generated using an algorithm such as ECDSA (Elliptic Curve Digital Signature Algorithm).
Sample Private Key
b5ba96aae89dc703c27ec5b3d478a8b176b874f248c83e533d9edc18e6356d44
The private key is what you would need to digitally "sign" transactions i.e. to send crypto to someone else.
If someone gets hold of your private key, they can transfer all your crypto to another address.
This is what happens in most crypto ‘hacks’.
That's why we say that "Not your keys, not your coins".
Sample Public Key
02b90ecf13d0ef14cd777f3a427b712ddd46703375f458092714c1c72106803ca2
The public key is used to verify the digital signature. It proves ownership of the private key.
Sample WIF
L3Jy6k2KCJ6uDNEj1hirw49sPWghT7Cg77rSDvfpAkAC7F63PhGe
A "Wallet Import Format" (wif) is a shorter version of a private key.
Sample Address
1AAE1EDcCAUmyBfi46G3vpik8oCaKVoabT
The address is similar to your bank account or UPI ID. Anyone can send crypto to your address. The address is derived from the public key.
If you send crypto to the "wrong" address, it’s gone forever!
10. Blockchain Wallets
A blockchain wallet is designed to:
store your public and private keys,
send and receive cryptos,
monitor ‘balances’, and
interact with supported blockchains.
There are 4 main types of wallets:
Paper Wallets
Hardware Wallets
Software Wallets
Exchange Wallets
A hot wallet is one that is connected to the Internet and is considered the most vulnerable to hacking.
Examples: Software Wallets, Exchange Wallets.
A cold wallet is not connected to the Internet and is considered more secure.
Examples: Paper Wallets, Hardware Wallets,
Paper wallets are inconvenient to use but are the safest option. Consider using them if you have a large number of crypto assets to keep for a long period of time.
BitAddress is a JavaScript Client-Side Bitcoin Wallet Generator.
You can use it to generate Bitcoin addresses and their corresponding private keys in a web browser.
Site: https://www.bitaddress.org
To generate a Bitcoin address and its corresponding private key, simply move your mouse randomly on the bitaddress page.
A wallet will be generated in your web browser. It will look something like this:
Hardware wallets are a little pricey and there’s always the risk of losing or breaking them.
Software wallets are free & easy to use. But if you accidentally delete them, your crypto is gone forever.
Examples: Trust Wallet, Metamask
So remember to back up the seed phrase - a bunch of words that you can write down. Example:
history
lumber
quote
board
young
dove
robust
kit
invite
plastic
regular
skull
Wallets provided by Crypto Exchanges are called "custodial" because the private keys are under the control of the Exchange.
If they go bankrupt, you lose all your crypto.
Remember: Not your keys, not your coins.
11. Blockchain Record-keeping Models
Accounting or record-keeping methods are used by blockchains to determine the provenance and ownership of coins in the network.
3 types of record-keeping models are used in blockchain networks:
UTXO (Unspent Transaction Output) Model e.g. Bitcoin
Account/Balance Model e.g. Ethereum
Hybrid e.g. Cardano
Each Bitcoin transaction spends output from prior transactions.
Each Bitcoin transaction also generates new outputs that can be spent by transactions in the future.
A Bitcoin user’s wallet keeps track of all unspent transactions associated with all addresses owned by the user.
The balance of the wallet is the sum of those unspent transactions.
UTXO can be compared to spending banknotes and getting back change.
The account / balance model can be compared to spending using a debit or credit card.
The benefits of the UTXO Model are scalability and privacy (if the user uses new addresses for each transaction).
The benefits of the account / balance model are simplicity and efficiency.
Bitcoin derivatives such as Bitcoin Cash, Zcash, Litecoin, Dogecoin, Dash, etc. are UTXO chains.
Ethereum, EOS, Tron, and Ethereum Classic are account-based chains.
Cardano, Komodo, Tron, and Qtum use a hybrid model.
12. Blockchain v DLT
All Blockchains are DLTs, but all DLTs are not Blockchains
Many of us use the terms "Blockchain" and "Distributed Ledger Technology" (DLTs) interchangeably. But there are a few very important differences.
A blockchain:
is a linear, chronological structure
consists of blocks of data (transactions) that are chained together.
In my personal opinion, Blockchain is suited for 1 use case only - smart asset lifecycle management.
Blockchain increases transparency and reduces the need for intermediaries in financial use cases.
While Blockchains have a linear chronological structure, DLTs can have different structures, such as:
Graph e.g. IOTA
Mesh e.g. Holochain
Tree e.g. Corda
DLTs are suited for multiple use cases such as:
Supply Chain Management
Identity and Verification
Healthcare
Government and Public services
13. What do Blockchain Developers Build?
1. Crypto Wallets like Metamask & Trust Wallet
2. Crypto-powered payment systems
3. Fungible Tokens (ERC-20 or compatible)
4. NFTs (ERC-721 or compatible)
5. Multi Tokens (ERC-1155 or compatible)
6. NFT Marketplaces
7. Play to Earn, Learn & Earn, and Move to Earn platforms
8. Crypto investing apps
9. Customized private & public blockchains on platforms like Avalanche
10. Smart Contract enabled insurance services
11. Decentralized Autonomous Organizations (DAOs)
12. Decentralized Naming Solutions like ENS
13. Web3 projects like decentralized identity, storage, video & music platforms
14. DeFi projects like bridges, exchanges, farms, lending & staking platforms
15. Oracles like Chainlink
16. Scaling solutions like Plasma Chains, zk- Rollups, and Optimistic Rollups
17. Metaverse and in-game assets
14. Blockchain use-cases
Govt of India's National Strategy on Blockchain lists 44 use cases
Transfer of land records / property
Digital certificates management
Pharmaceutical supply chain
e-Notary service
Blockchain-enabled e-Sign solution
Farm Insurance
Identity management
Duty payments
Automated customs enforcement and compliance
Agriculture / farm produce supply chains
E-Voting
Smart Grid applications include energy transmission, distribution, trading, and marketing of energy
Authorized access to relaying in the substation protection system
Government crypto wallet platform for selling, buying, and trading
Multiple layer and multiple level access Blockchain-based cloud storage of health test records
Validation of Bill of Lading in cross-border transport
Ease of validation of documents at the customs at the ports of entry and exit
Electronic health record management
Digital evidence management system
Public service delivery
Blockchain for social good use cases (charity, donations)
Metering and settlement
Payment security mechanism
Authentication and authorization services
Automated control of decentralized power
Smart grid application and grid management
Microfinance for Self-Help Groups (SHG)
Customs and trade finance
Cross border trade
Renewable energy trading and management
Insurance underwriting and claims management
Aggrotech environment
Micro-financing, financing small businesses or individuals
Secured logistics document exchange (SLDE)
Cold chain for supply chain
National and state highways, toll collection, tracking of public infrastructure
Blockchain for urban development tracking through Public Private Partnership
Tracking the progress on climate agreement through Blockchain
Asset transfer across different government departments
Digital identities, and verifiable credentials to secure privacy and enable new use cases
Safe and secure vaccine distribution and administration
IoT device management and security
Vehicle lifecycle management
Chit fund operation and administration






Thanks Rohas for sharing. It's really amazing & valuable. Would love to read more : )
Thank you